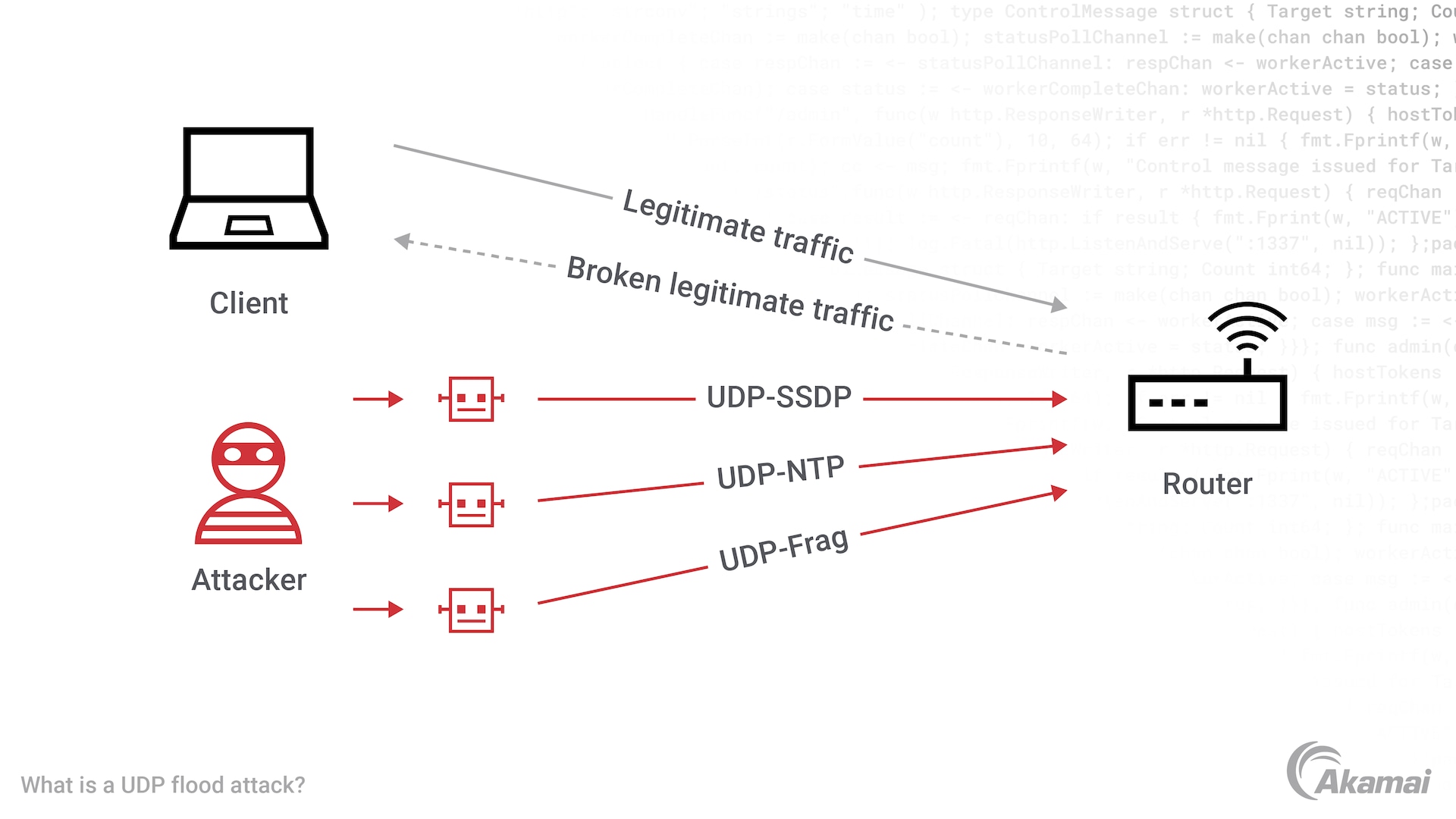
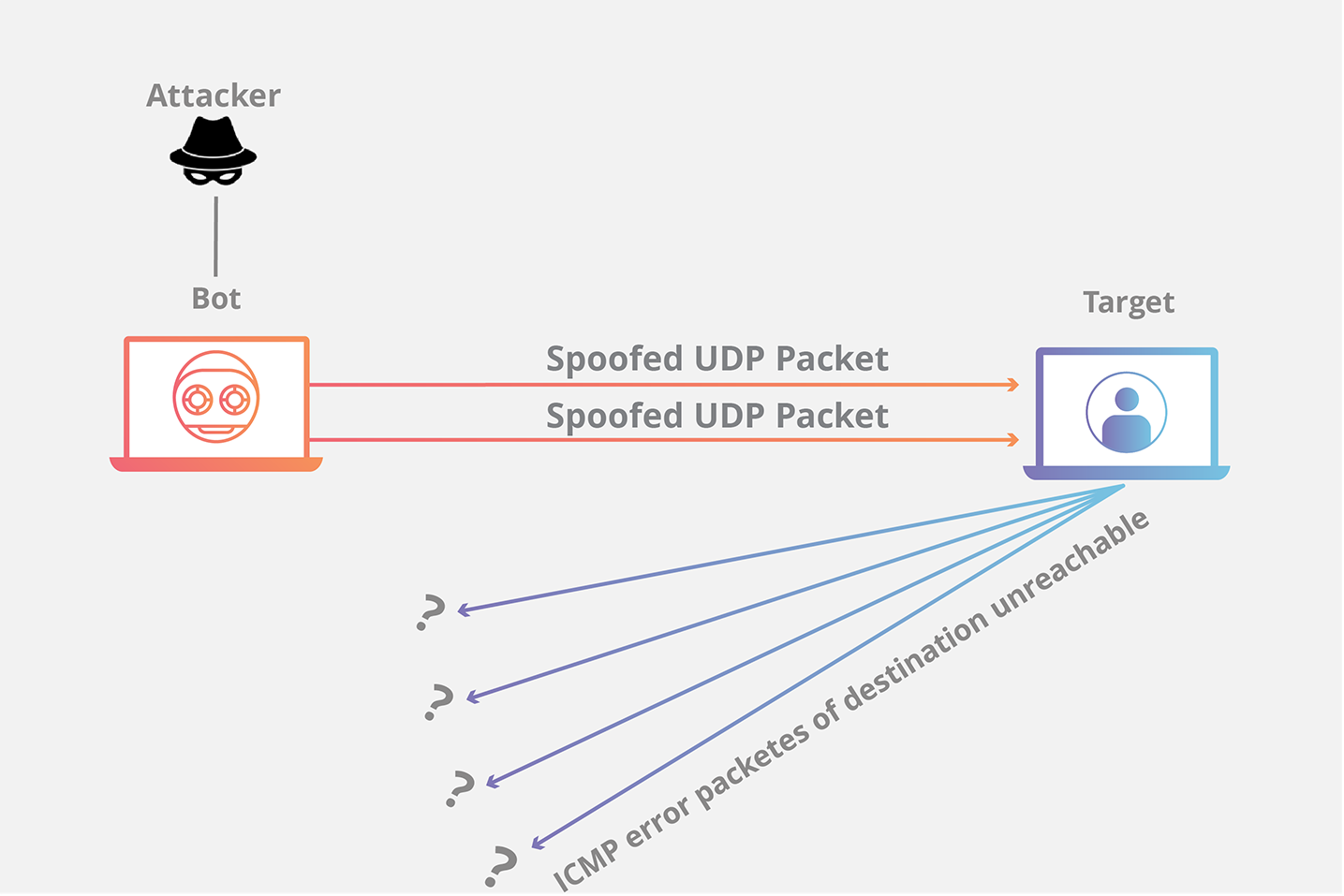
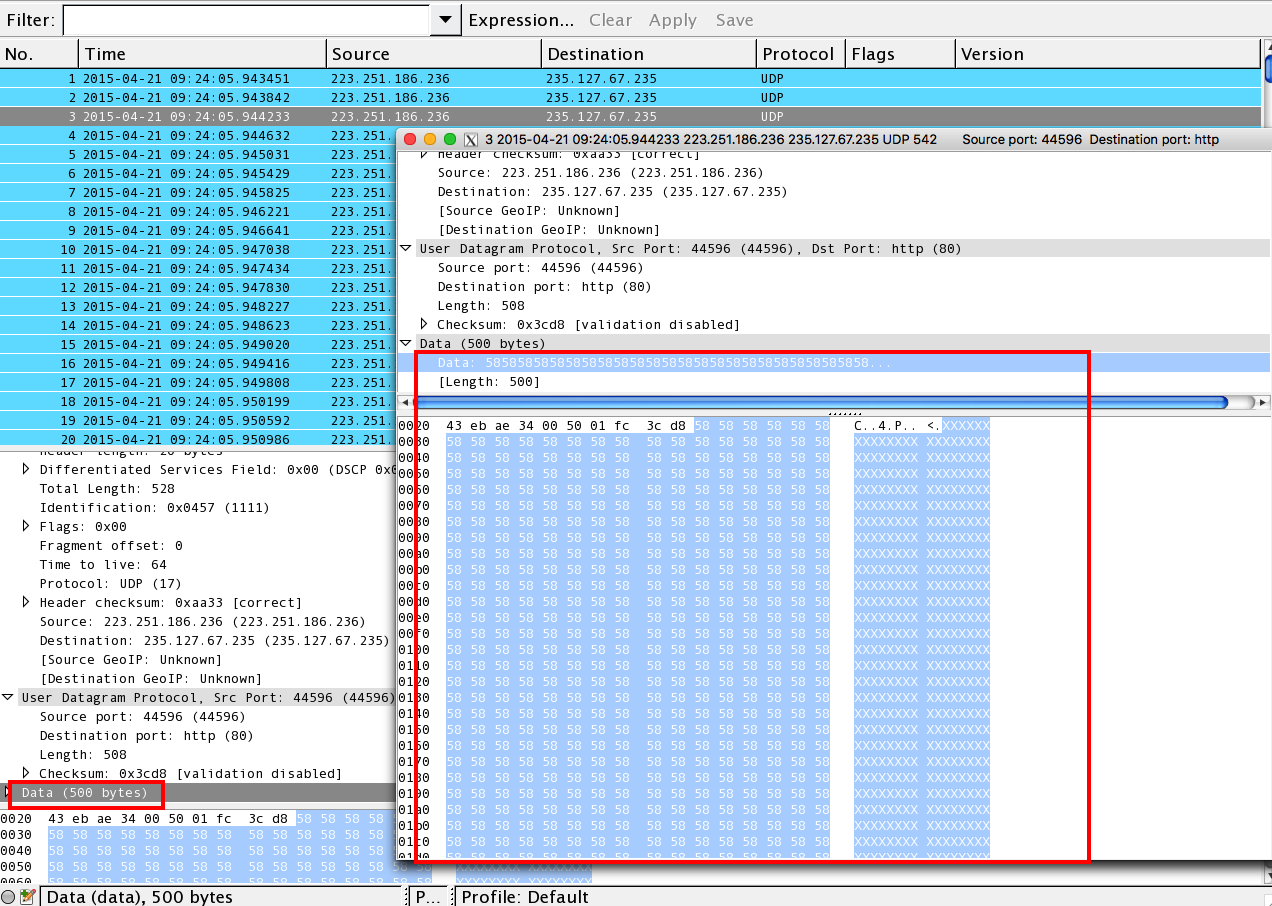
Basic UDP Flood Attack. DDOS and Anti-DDOS methods. Articole introductive si ajutor | Evidweb Network
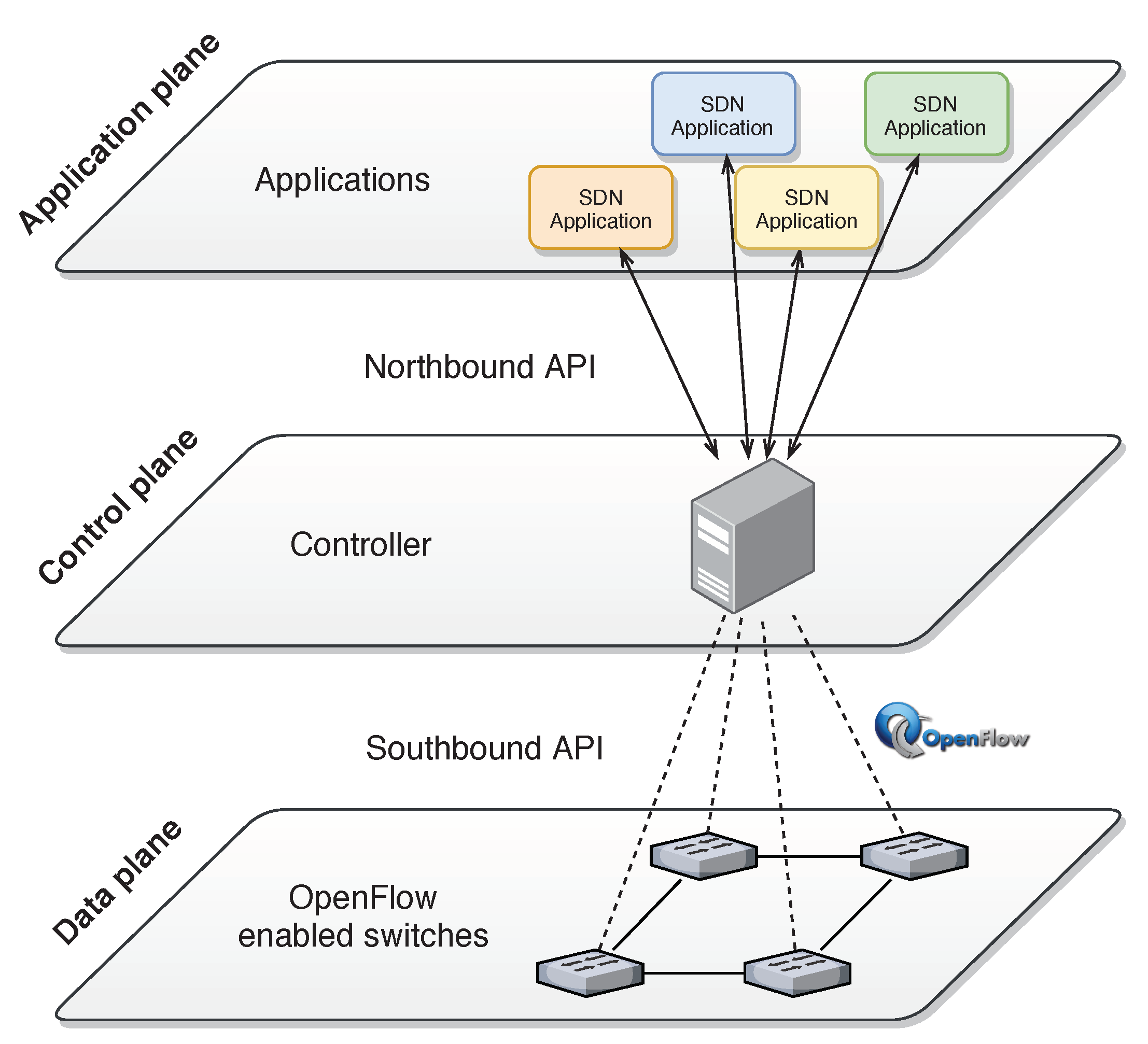
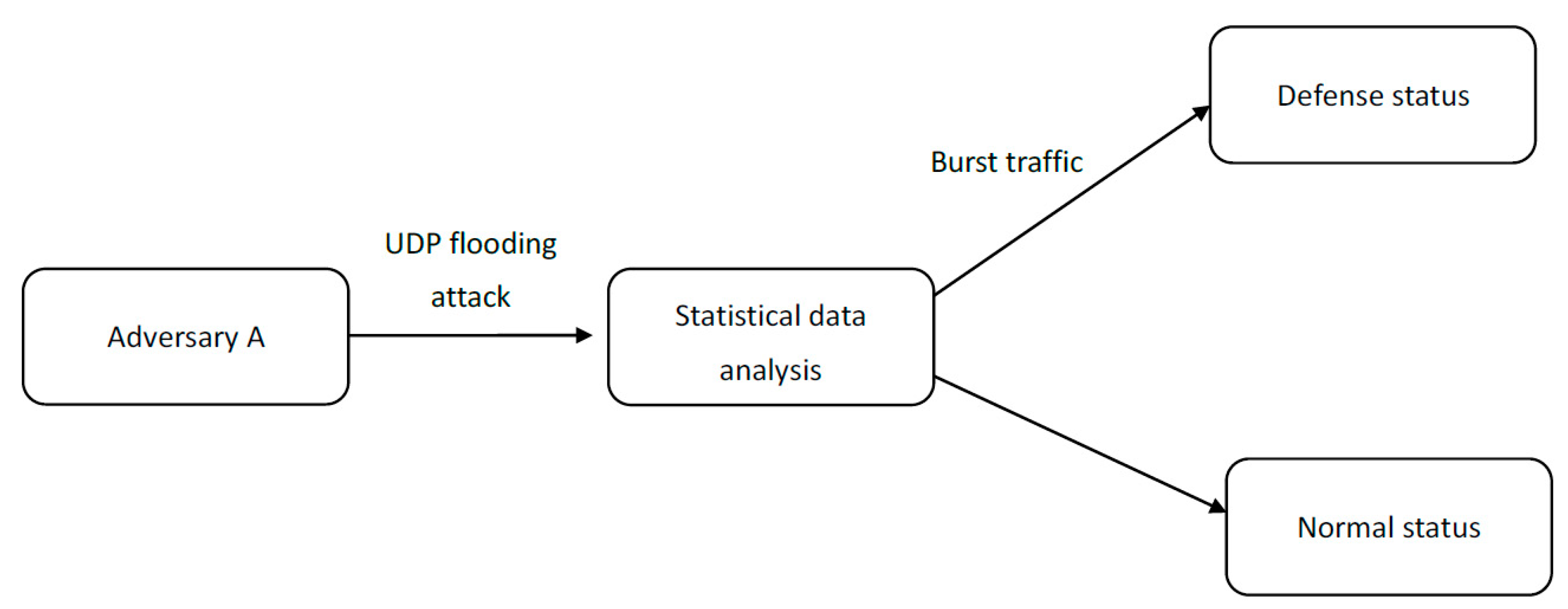
Sensors | Free Full-Text | Detection and Mitigation of DoS and DDoS Attacks in IoT-Based Stateful SDN: An Experimental Approach
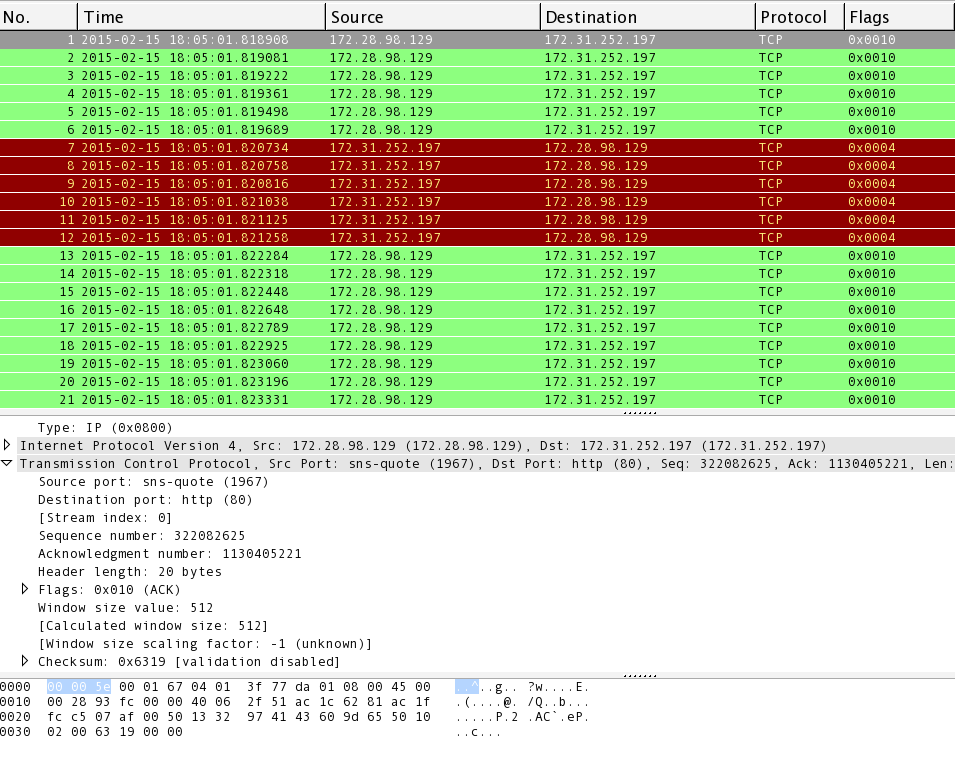
How do threat logs look like if UDP flood detected by Classifie... - Knowledge Base - Palo Alto Networks
How do threat logs look like if UDP flood detected by Classifie... - Knowledge Base - Palo Alto Networks
How do threat logs look like if UDP flood detected by Classifie... - Knowledge Base - Palo Alto Networks