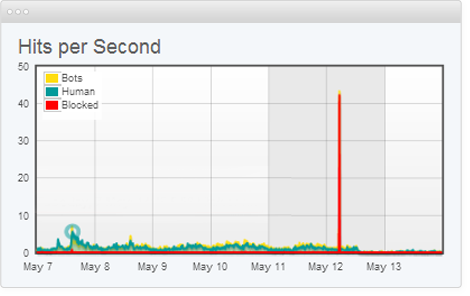
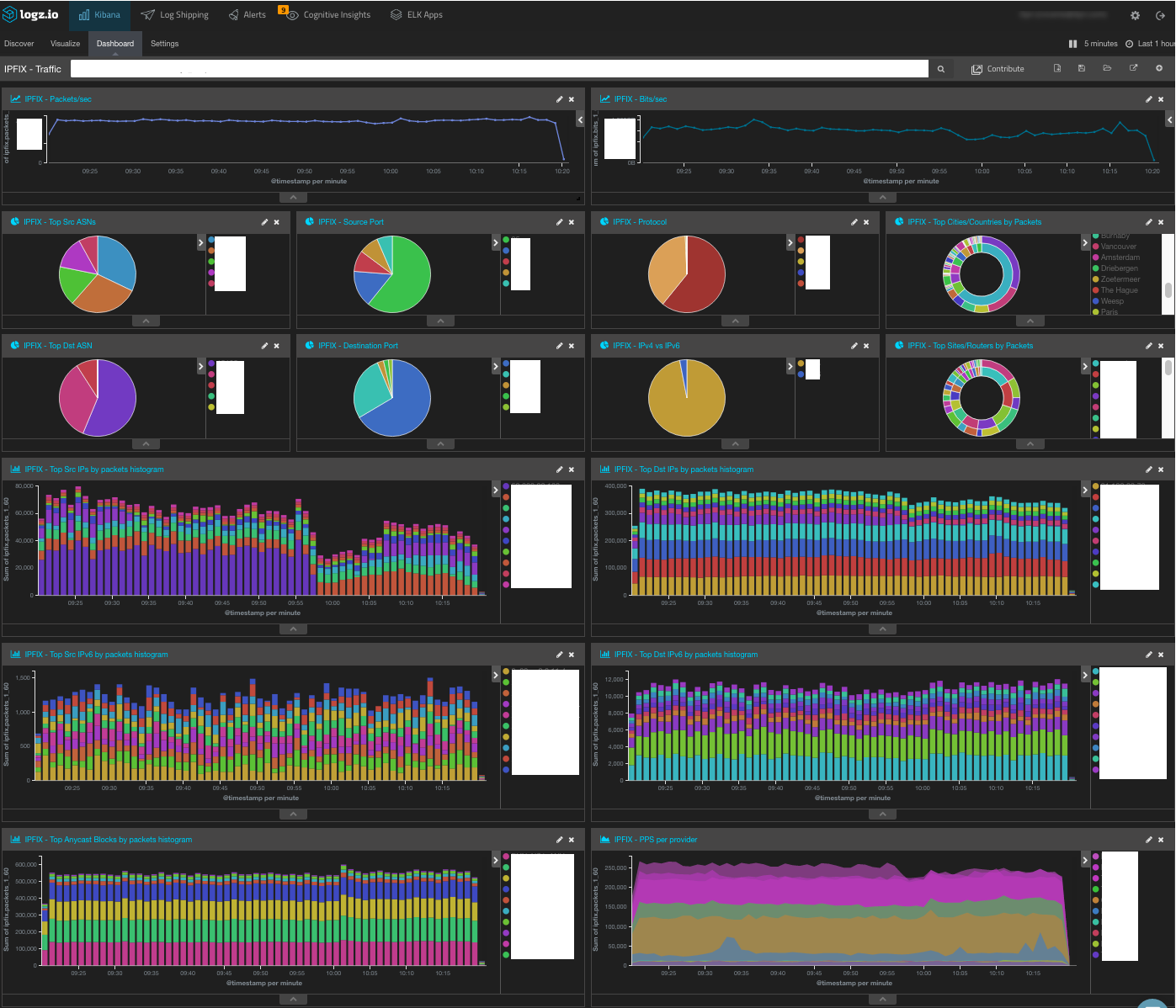
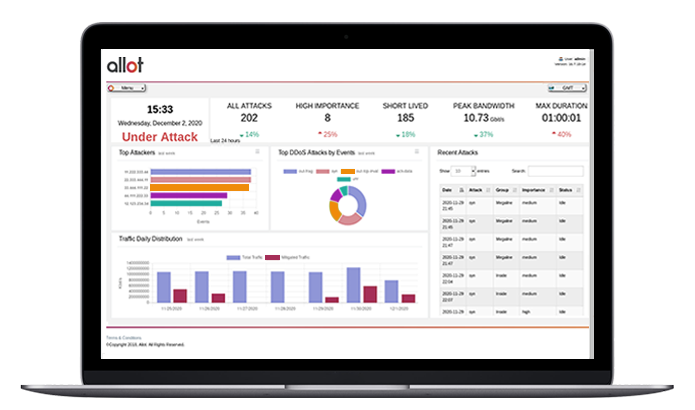
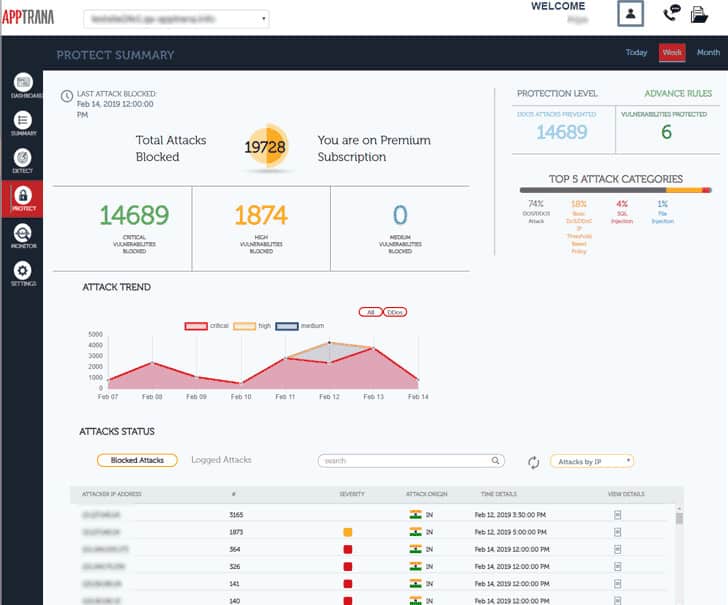
How to Thwart DDoS Attacks from Hitting Critical Infrastructure - Interconnections - The Equinix Blog

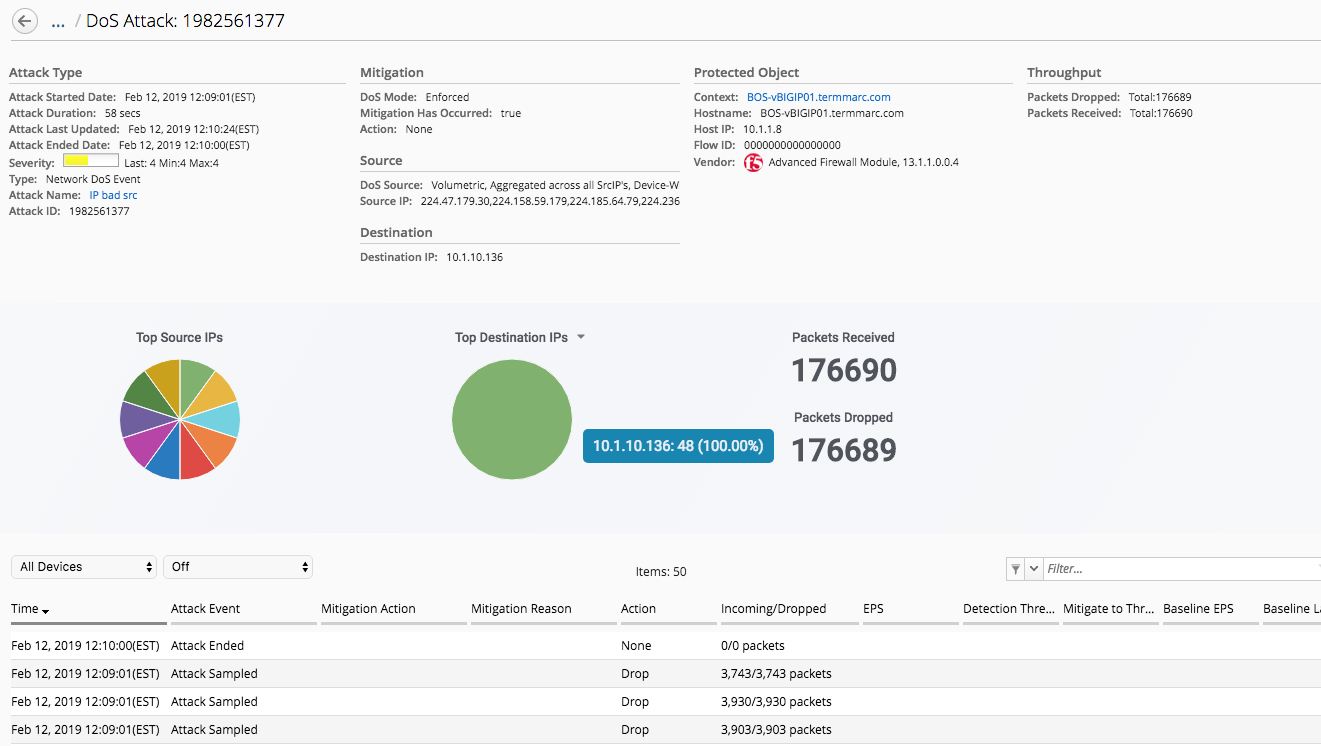
Set up centralized monitoring for DDoS events and auto-remediate noncompliant resources | AWS Security Blog
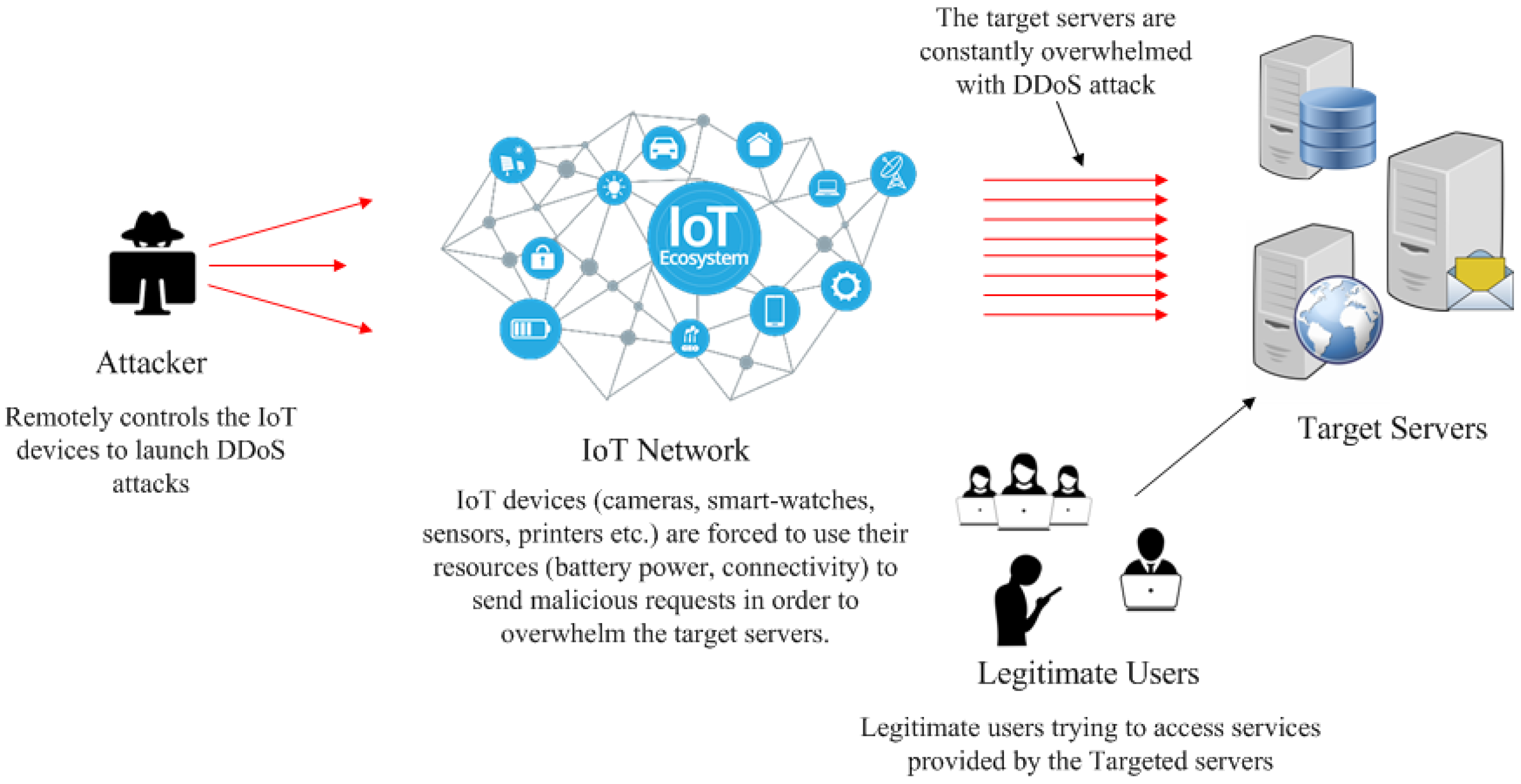
Sensors | Free Full-Text | Blockchain Based Solutions to Mitigate Distributed Denial of Service (DDoS) Attacks in the Internet of Things (IoT): A Survey