
How to Catch the Top OWASP 2021 Security Category - Broken Access Control - in Code Review | PullRequest Blog

Switch Port Security Access Control List (ACL) Configuration on Cisco... | Download Scientific Diagram

TAS2505EVM: (Codec Control Tools) Access violation at adress ERROR - Audio forum - Audio - TI E2E support forums
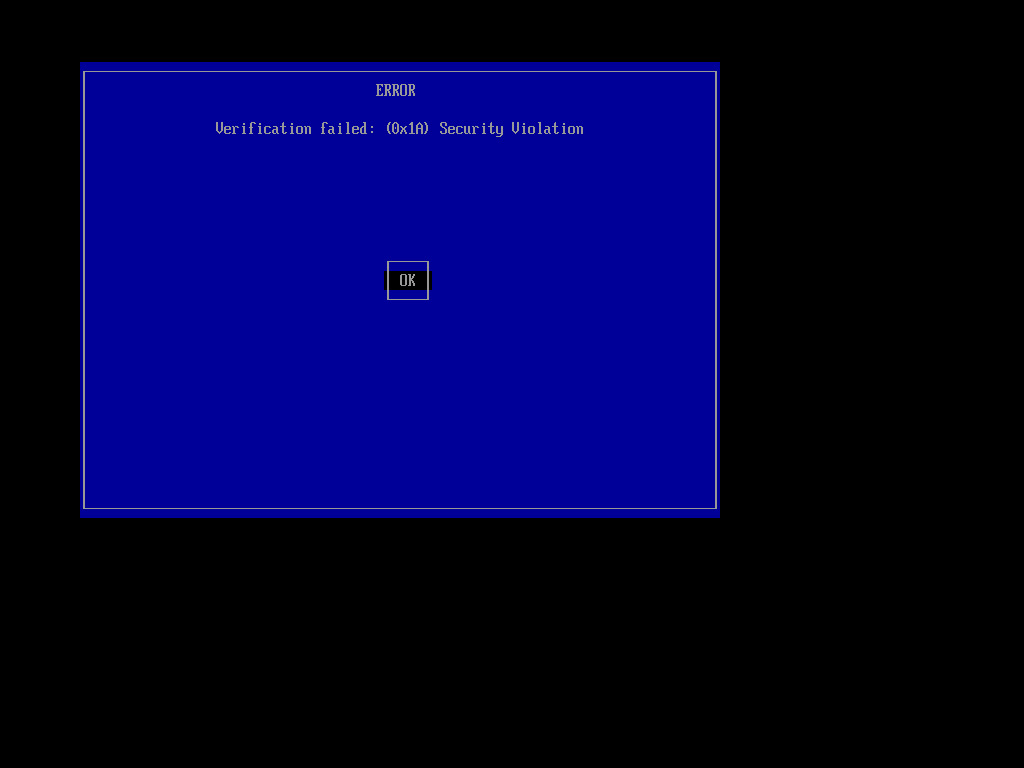
System boot fails due to Security Violation of shim caused by SbatLevel UEFI variable left from some other OS - Red Hat Customer Portal

Kai Bu 12 Protection & Security The last topic to be covered in this course would be protection and. - ppt download

Internetworks: What is cisco port security? How to secure switches ports? | What are the violations of port security? | How to configure?



![FIXED] Best Solutions to the "Access Violation at Address" Error FIXED] Best Solutions to the "Access Violation at Address" Error](https://www.auslogics.com/en/articles/wp-content/uploads/2022/09/access-violation_3.png)







![FIXED] Best Solutions to the "Access Violation at Address" Error FIXED] Best Solutions to the "Access Violation at Address" Error](https://www.auslogics.com/en/articles/wp-content/uploads/2022/09/access-violation_2.png)

![FIXED] Best Solutions to the "Access Violation at Address" Error FIXED] Best Solutions to the "Access Violation at Address" Error](https://www.auslogics.com/en/articles/wp-content/uploads/2021/04/fix-access-violation-at-address.jpg)


